Cybersecurity requires seeing the attacker’s point of view – and how IT Architecture achieves this
If your data could be valuable to someone else, it’s likely that someone will try to find the vulnerabilities in your architecture. Before that happens, one of your best lines of defence will be to understand your own IT architecture better than they do.
In his book “A Burglar's Guide to the City”, Geoff Manaugh describes the case of a thief who burgled a whole row of adjoining flats [1]. Instead of breaking into each property from the outside, he broke into one and then entered the next one by simply cutting through the relatively weak internal walls. The so-called “drywall” burglar did this repeatedly until he got to the end of the block, carrying the stolen goods back through his "tunnel" at leisure.
Consider the cybersecurity problem early
Householders are often advised to upgrade their door and window locks to deter burglars. However, it’s difficult to re-fit internal walls to stop an intruder. If the housebuilders didn't consider the problem during construction, it may not be feasible to fix it later.
Cybersecurity experts emphasize the importance of applying security principles to a system's architecture early in its development, at the design and build stages.
The first principle recommended in the NCSC’s cybersecurity guidance is establishing a system's context before designing it using IT Architecture. The context includes an understanding of the system's threat model. The guidance suggests applying appropriate modeling techniques to understand how an attacker could achieve their objectives and the level of capability such an attack would require.
Security controls can then be mapped to potential attack points to establish confidence in the resilience of the design.
As an architect, design the system from an attacker's point of view
Doing this effectively requires architects and designers to view the system from an attacker's point of view. In practice, this can be difficult simply because it involves a radical mindset change.
The "drywall” burglar's technique succeeded because the house builders and property owners didn't consider the internal wall construction as a vulnerability that was likely to be exploited by an intruder. Criminals can be very creative when it comes to identifying weak points. At one time or another, many types of standard building features, including sewers, rooftops, air-conditioning ducts, garbage chutes, and even wall cavities, have all been "re-purposed” as access routes by burglars.
Manaugh, a writer specializing in architecture and the built environment, regards burglary as an essentially "architectural" crime. It depends on the burglar appreciating a building's architecture, which can be fundamentally different from that of the building's legitimate users. In his words, burglary is "topology pursued by other means: a new science of the city, proceeding by way of shortcuts, splices and wormholes". To a burglar, a roof can become an entryway, a wall can become a door, and he can make one if a corridor doesn't exist.
How cyberattacks happen
Cyberattackers apply the same treatment to computer systems and networks. John Lambert of the Microsoft Threat Intelligence Center summarises the approach: “Assets are connected to each other by security relationships. Attackers breach a network by landing somewhere in the graph using a technique such as spearphishing, and they hack, finding vulnerable systems by navigating the graph. Who creates this graph? You do.” [3]
Attackers exploit the security relationships between systems, not just legitimate users' "authorized” paths. The graph of connections should be constrained by the IT architecture and changed according to the enterprise's needs. However, it can also be modified inadvertently or maliciously, for example, by installing software containing a vulnerability that can be exploited to access other network assets.
How can IT architecture help you protect against an attack?
One approach is to build your own graphs to help visualize attack paths. A graph allows you to see the routes to potential targets. This produces a view corresponding to the one an attacker tries to construct by exploring your network. You can then take appropriate actions, for example, by breaking connections to reduce the number of attack paths and hardening key nodes' security.
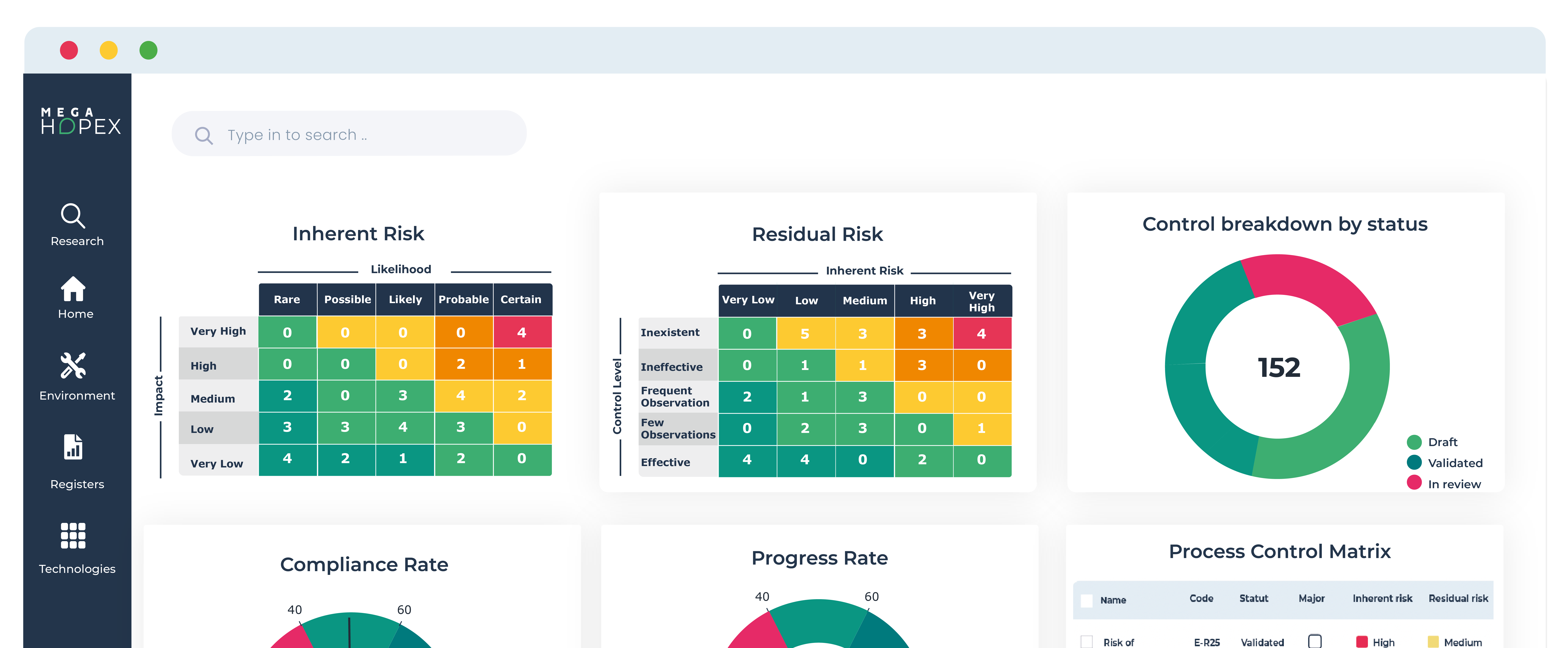
Some tools can generate graphs from dependencies that exist in your networks. However, to identify the connections your organization requires, you must compare these with your IT architecture. Solutions such as HOPEX show how your IT assets are connected and how those assets support your business.
If your data could be valuable to someone else, someone will likely try to find the vulnerabilities in your architecture. Before that happens, one of your best lines of defense will be to understand your own architecture better than they do.
Strengthen cyber resilience with an integrated solution

A five-step approach to strengthen your company's cyber resilience, offering key benefits:
- Protect organizations from cyber disruptions
- Comply with cyber resilience regulations
- Align cyber resilience management with business objectives
- Maintain a proactive cyber resilience stance
Governance, Risk and Compliance Related Content
Enhance operational resilience using integrated risk management
MEGA HOPEX for GRC
Request a demonstration of HOPEX for GRC, and see how you can have immediate value of your projects.